
Data breaches and hacking put companies in jeopardy of exposing critical business information or can cause damage to company operations. While the most visible cases relate to computer databases, data transmitted over any network can be captured by an outside intruder. Attacks on wireless sensing and control networks also can cause an unintended system operation, affecting production loss or safety issues.
As the use of wireless technology for sensing and control systems becomes a more common practice in various industries such as oil and gas, agriculture, water systems, forestry, and public infrastructures, security becomes an important issue to ensure the authenticity of data as it passes from device to device. Information that passes through a wireless remote monitoring system must be validated and move untampered with through different transmission points. Safeguards must prevent malicious attackers from intercepting a data packet and intentionally changing its contents.
Using data without an integrity check is risky as it can cause unknown actions. Unfortunately, many companies using remote monitoring and control systems do not consider security protocols to protect their data.
A typical wireless remote monitoring and control system (see Figure 1) consists of a gateway and remote nodes that interface with sensors to provide field data and to control devices such as pumps, valves, fans, and lighting. As gateways can accommodate hundreds or even thousands of transceiver nodes, critical process and control data can be transmitted over large geographic areas covering hundreds of square miles. A series of security checks are necessary to protect data as it passes from point to point. As the wireless data is typically carried by a low power wireless sensor network, the wireless network, itself, must be responsible for protecting this information. Once the wireless data reaches a gateway, standard Ethernet security practices can be applied, consistent with company IT policies.
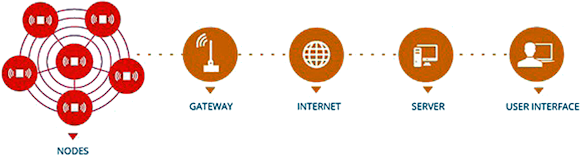
Fig. 1: Pictured is a configuration of a wireless remote monitoring and control system. Security for the wireless sensor network falls outside of IT security applied to the data from the Gateway to the server and user interface. Therefore, security measures must be evaluated on their own.
Next page
Types of Data Threats
A variety of data intrusions can interrupt a wireless sensor network, jeopardizing the reliability of output and even the production process. For example, in a replay attack, a device captures an encrypted message and retransmits it later to the network, with potential serious effects. Should a simple, high-pressure signal from a device be captured and later retransmitted, a control device could incorrectly trigger a shutoff, potentially causing lost production or a safety issue.
Best Practices
Security used by a wireless sensor network must include more than just encryption. Device authentication and replay prevention also are important security features necessary to secure a system. Discuss the security features with your vendor to insure that proper security measures protect your data network. Here follows some best practices to consider.
- Data Encryption protects electronic data from intrusion and ensures only designated recipients can read the information. AES Encryption supports a highly reliable and secure wireless network within the entire wireless system. The encryption protects against tampering as any modified data is invalidated and ignored. AES encryption is typically chosen for wireless sensor networks as it provides a high level of security and can be implemented on low power sensor devices.
- Device Authentication ensures that nodes perform an integrity check before joining the network. This security measure prevents nodes from joining a rogue or malicious network that would keep them from communicating with their intended network. Additionally, this process allows only authenticated nodes to connect to the network.
- Replay Prevention, as previously discussed, stops messages from being resent by a malicious device. It blocks security attacks if packets are captured and retransmitted at a later time. For example, if a message "to turn on a relay" is captured and sent later, operations could be at risk. Reply prevention schemes are typically based on time synchronization of all nodes in the network or message sequence numbers, allowing only fresh messages to be accepted by the network.
Next page

Fig.: 2: Signal Fire Wireless Telemetry uses firmware including data encryption and device authentication on its wireless remote monitoring products for a more reliable and secure wireless network infrastructure.
Conclusion
As the use of wireless sensor networks become more prevalent in monitoring and control applications, they become a bigger target for attacks. As no security standard exists in the industry for these networks, some do not utilize any protection at all.
Don't assume security is already in place or extensive enough to protect your important data and processes. Consider the security employed by the wireless network in addition to your corporate IT.
While sophisticated to provide robust data protection, security should be easily configurable and deployed. Consider the type of data and control messages that the wireless sensor network will transmit and evaluate the possible consequences of not properly securing that data. In almost all cases, data breaches or attacks put operations at risk. Even in remote locations, threats can happen.
About the Author
Josh Schadel serves as Director of Engineering at SignalFire Wireless Telemetry responsible for the development of new products from concept through production. With over 15 years experience in high tech instrumentation, he has a strong background in embedded systems and PCB designs as well as sensor networks. SignalFire Wireless Telemetry designs and manufactures wireless telemetry products that enable robust, long-distance wireless communication connecting multiple devices in challenging outdoor environments. Contact the company at [email protected] or visit http://www.signal-fire.com.
Related Stories
90% of Employees Bypass Security
In the IoT & Beyond, Security Resides On The Dark Side, Part One
In the IoT & Beyond, Security Resides On The Dark Side, Part Two
In the IoT & Beyond, Security Resides On The Dark Side, Part Three
Tech Giants Collaborate on Zero Outage to Define New Industry Standard