On July 31, 2017 HBO became the latest high-profile victim of data theft, however the loss of valuable commercial or personal information is just the tip of the iceberg when it comes to what hackers could do. Here we’ll look at the devastating potential impact of a breach on our physical or virtual infrastructures, and what we can do to safeguard our essential utilities.
The Cybercrime Crisis
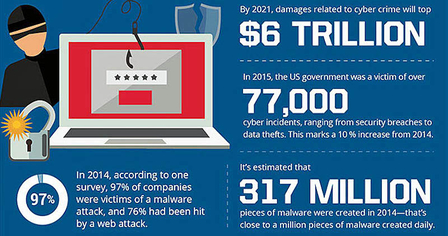
Hackers claim to have access to a huge 1.5 terabytes (TB) of data from HBO, which dwarfs even the 2014 Sony hack, when around 200 GB were stolen. It’s not just big companies being targeted and held to ransom though. At least 97% of companies say they have been subject to some kind of malware attack. The US government has seen an increasing number of incidents, and as we saw with WannaCry, the infection of organizations such as the National Health Service in the UK can directly affect our front-line services (fig. 1).
The sophistication of these attacks mean the cybersecurity industry is playing catch-up, and we are unlikely to see the number of breaches diminish anytime soon. Cybercrime is estimated to cost the global economy $400 billion a year, but that figure is rising all the time, and total related damages may top $6 trillion by 2021 according to a report from Cybersecurity Ventures.
The worry is, that in their search for ever higher ransoms, hackers may turn their attention to utilities that we cannot do without. Imagine the public pressure to pay them if our water supply was cut off for example. Terrorists or state-sponsored hackers might look to do the same as a way of causing disruption and economic damage to their opponents.
Security Vulnerabilities
Unfortunately, new technologies can play a significant role in exposing our infrastructure to this kind of attack. Networks which connect different industrial facilities and allow remote access have helped improve efficiency and reduce costs, but also provide a point of entry for hackers. When infrastructure is connected to the Internet, attacks can be launched from anywhere in the world. Not only that, but many industrial control systems are vulnerable because they are typically older, and don’t have the latest software updates and security patches. Installation of any new feature is time-consuming, complex, and requires extensive testing, so given the limited downtime available, they often don’t get applied immediately.
What may pose an even bigger risk is the advent of the Internet of Things (IoT). There is major concern that many products are being developed with a lack of basic security, and with a predicted 50 billion connected devices by 2020, that is a huge number of vulnerabilities hackers could exploit.
A recent Tripwire survey found that 96% of IT security professionals expect to see an increase in attacks on the industrial IoT, essentially those devices that are connected to our infrastructure. These IoT products can also be hijacked to perform powerful distributed denial of service (DDoS) attacks, with thousands or even millions of malicious endpoints.
Physical Infrastructure
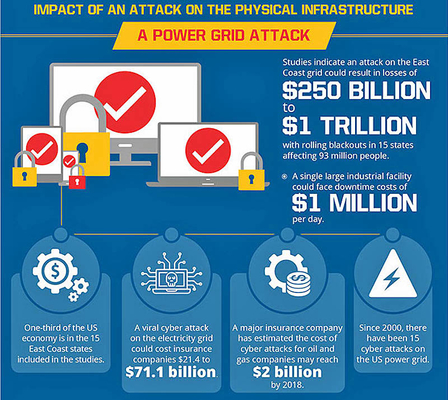
A successful cyberattack on the US power grid would have a huge financial impact, one study suggesting an outage on the East Coast could result in losses up to $1 trillion. Incidents are on the rise in the oil and gas industries as well, increasing costs and driving up prices. But the potential damage is not only financial. For example, Verizon recently revealed that hackers had exploited old operating systems and an even older server to take control of a water treatment plant. Verizon didn’t reveal the name or location of the water company in question.
The attackers could’ve altered the chemical composition of the water supply, but luckily it doesn’t appear they knew how to do that. Inversely, the knowledge to do so would be deadly in the wrong hands. Similarly extended blackouts could also threaten public health.
One risk is that sophisticated state-sponsored techniques could become more widely available. The US and Israel used malicious code to destroy Iranian nuclear centrifuges in 2009, while many believe Russia was behind power outages in Ukraine in 2015 and 2016. The worrying thing is that cybersecurity researchers now think that latter attack was designed to test a piece of malware purpose-built to disrupt physical infrastructure systems. It was automated, and contained adaptable components that could allow it to be used in other power grids around the world, including in the US.
Virtual Infrastructure
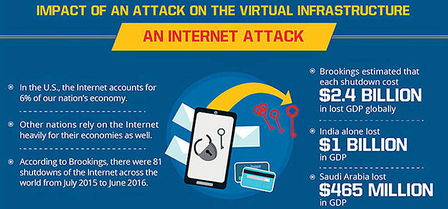
Just for a second, try to imagine living without the Internet; difficult, right? It has become such an integral part of modern life that it is increasingly considered an essential public utility. As a matter of fact, the United Nations considers internet access a human right.
An internet shutdown can cause huge economic damage and social disruption, making it a target for a range of cybercriminals. A Brookings study found that shutdowns in 2016 cost $2.4 billion dollars in lost GDP globally, and that does not include the impact of reduced worker/business productivity or the loss of investor confidence.
Recent incidents offer a warning about how hackers might go about such attacks. In October 2016 major sites such as Twitter, CNN and Netflix were brought down by the Mirai botnet, a huge DDoS attack which was powered by those vulnerable IoT devices and hit the domain name system (DNS) infrastructure. Satellites, which control most of the world’s communication networks as well as critical defense, transport, and business systems, are another potential target.
What Can We Do?
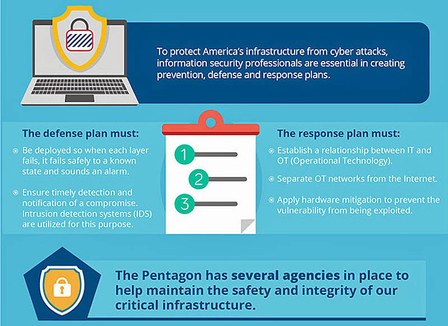
Although the task of securing our infrastructure is a difficult one, many defense measures can be put in place. They should cover the prevention of attacks with updated IT systems and better security, the rapid detection and notification of breaches, and an effective response plan. Critically, that response plan must include both the immediate separation of hardware from the Internet, and offline backup systems. The Pentagon has a number of agencies in place to implement these measures, and the US Energy Department says it is helping power firms defend against cyberattacks.
However, one thing that may compromise our defenses is the fact that there is currently a serious shortage of cybersecurity professionals available. In the US alone in 2015 there were 209,000 unfilled positions, and demand is rising fast, so we desperately need to train more people with the right skills.
We also need cybersecurity researchers who work at the cutting edge of the field in order to develop innovative new solutions; China for example is looking to secure its satellite communications with a quantum satellite, used to send potentially un-hackable communications. Because the costs of data theft are already well-established in fields like finance and healthcare, and roles in those industries are well-paid as a result, utility providers face a challenge in recruiting the right talent. However, it is a matter of national security that that challenge is met.