The potential for quantum computing to break classical computer security is spurring efforts to reimagine it, but fortunately there’s time before bad actors can cost-effectively exploit quantum to do much damage.
Cracking currently used cryptosystems was one of the first famous applications of quantum computing, and has been viewed as a “good accident,” Hari Krovi, lead scientist at Riverlane, told Fierce Electronics in an interview. “It's great that we know that this can crack cryptography.”
He said this discovery has spurred research in into post-quantum cryptosystems – those computers that will remain that secure in the quantum era, which The National Institute of Standards and Technology (NIST) in the U.S. is tracking as it works to solidify standards.
Error correction capabilities key to quantum applications advances
Riverlane is focused on solving error correction, which Krovi said is quantum computing’s defining challenge, by building a quantum error correction stack to enable fault-tolerant quantum computing.
Part of this work is the estimation of resources needed for different quantum computing applications like simulations of physical systems, and how many fault-tolerant operations will be needed for any given application, he said. “This informs you how soon or how far away applications are.”
These estimates include the ability to cost-effectively use quantum computing to hack classical computing security. Krovi said finding new quantum algorithms is not so easy, and you want those algorithms to be better than what is already available. “We have many constraints.” He said there’s not much point in building a quantum computer to do the same thing as an existing supercomputer.
Knowing that quantum computers could break current cryptography has heightened the need to get a clear understanding what quantum computing is capable of.
In the meantime, developing security that can protect systems from quantum computing threats is not unlike the Y2K problem – we have advance warning that there’s a problem that needs to be fixed.
Scott Best, technical director at Rambus, said the problem is that public key algorithms are based on math, and quantum computers love math. That means some common security public-key cryptosystems like RSA (Rivest–Shamir–Adleman) are more vulnerable than the Advanced Encryption Standard (AES) or Secure Hash Algorithms (SHA). “There's no like equation that describes what AES does,” he explained. “It doesn't have a lot to do with math.”
Rambus recently introduced its Quantum Safe Engine (QSE) for integration into hardware security elements in ASICs, SoCs and FPGAs in recognition that quantum computers will enable bad actors to break current asymmetric encryption. The QSE IP core uses NIST-selected quantum-resistant algorithms.
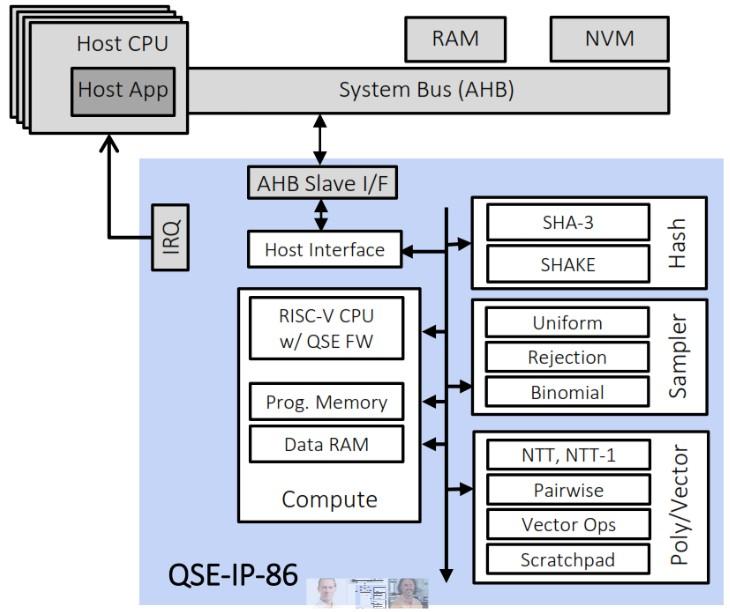
Best said cryptographers began seriously thinking about the quantum threat about six years ago with the expectation that quantum computing systems capable of cracking classical cryptography will be coming online in 2030. “We need to adapt new algorithms,” he said.
It also means updating the entire Internet, Best said. “Every browser session uses a key exchange mechanism,” he said. “We need to update all those firmware mechanisms. We need to revoke all the keys that are out there.”

The good new is that standards work has been in progress for some time. NIST put out a call for proposals in 2016 to find the best quantum-safe schemes to become the new cryptographic standards. The two primary standards the were chosen are the CRYSTALS-Kyber public-key encryption and the CRYSTALS-Dilithium digital signature algorithms.
Quantum-safe cryptography standards substitute the math problems that are easy for quantum computers to solve with math problems that are difficult for both classical and quantum computers to solve.
Hardware-level security is table stakes
Although these standards haven’t quite yet been finalized, Rambus has incorporated them into hardware accelerators, Best said. “We come from an environment where we do not trust software,” he said. “Software is always suspect.”
Best said a critical cryptographic operation should be done with tamper resistant hardware.
It’s also important that any added layer of security, whether it’s at the hardware or software level, doesn’t impede performance. “If you're setting up a key exchange, you want the key exchange to complete in 100 milliseconds,” Best said. “You don't want the key exchange to take several hours that feel like dial-up.”
These layers at the hardware level not only need to be done quickly, but also at low power, Codasip safety and security architect Carl Shaw told Fierce Electronics in an interview. Codasip is a processor technology company focused on enabling system-on-chip developers to differentiate their products, and that includes security features such as quantum resistant algorithms. “There's many ways we can customize the CPU,” he said.

One approach is to customize the actual core by adding instructions to provide an advantage on the numerical computing side because all these algorithms are very compute heavy, Shaw said. “We could also inherently change the micro architecture of the processor itself to make it more efficient to handle these sorts of computations or integrate in specific bits of hardware to help.”
Quantum could spot security vulnerabilities sooner
Codasip recently released its Capability Hardware Enhanced RISC Instructions (CHERI) security technology, which extends conventional hardware Instruction-Set Architectures (ISAs) with architectural features that enable fine-grained memory protection and highly scalable software compartmentalization. More simply, CHERI stops unsafe memory access that causes 70% of vulnerabilities.
Shaw said Codasip is keeping an eye on the specific bits of the quantum algorithms being used today, and so far, actual implementations are somewhat simple.
As much as quantum presents a threat to classical computing cryptography, Shaw thinks in the longer term that quantum computing will be valuable for identifying security vulnerabilities. “We're going to have something that is a lot more robust than what we have today.”
Rambus’ Best said it’s going to take time replace the existing public key infrastructure and revoke everything, but the technical community is doing the right thing. “Everybody recognizes the problem,” he said. “It's a bit of a race, but we think we can fix it.”