In the first part of this article, we discussed wireless networking terminology and the basics of mesh networking. Now we're ready to talk about some of the protocols involved.
Point-to-Multipoint
Key Characteristics. This is also known as a simple star and it isn't really a mesh network although it is often confused with one. Point-to-multipoint networks tend to use the modern air interfaces of either Frequency Hopping Spread Spectrum (FHSS) or Direct Sequence Spread Spectrum (DSSS, 802.15.4). They need to be statically configured for PAN ID, routes, and security. Note that all of the nodes can see other nodes and that they need to be told who to talk to. Security tends to be pair-wise for both the encryption and the key. End points may go to sleep or stay awake, but the central router is always awake.
Network Architecture. Figure 4 illustrates a typical topology. All nodes are on the same channel (or hop to the same channel) and bandwidth/throughput is limited by simultaneous data at the concentration point. Collisions happen with lots of traffic or lots of nodes.
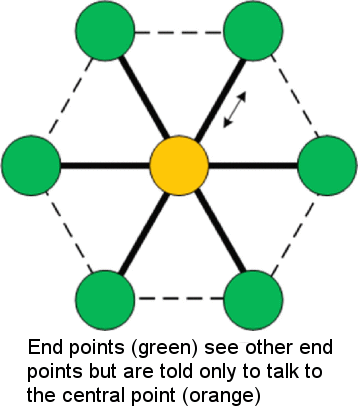 Figure 4. A typical point-to-multipoint topology |
Strengths. The beauty of the basic nonmesh point-to-multipoint network is simplicity. Communication, unless traffic is very heavy, is relatively deterministic because there are no hops and minimal or managed collisions. It also allows for maximum throughput because there is no added routing and no added route discovery. Finally, it is easy to understand and easy to manage. Because of this simplicity, it also tends to be the lowest cost for its specific size and function.
Limitations. Unfortunately, the simplicity also causes a number of limitations. The networks will tend to be small—large networks only work if polled from a central point and this requires very specific message management. There are also single points of failure and no ways to route around changing conditions. The network follows the belief that if it worked the first time, it will always work. Therefore, you must be sure of good RF conditions.
ZigBee PRO (ZigBee 2007)
Key Characteristics. ZigBee is built on top of 802.15.4 using DSSS in the 2.4 GHz band. End points sleep, routers don't sleep, and a coordinator is needed to start the network and to allow points to join the network. ZigBee has had three different versions of the standard—2004, 2006, and ZigBee PRO (ZigBee 2007). ZigBee 2004 is no longer used and ZigBee 2006 had significant limitations. ZigBee PRO includes key features for frequency agility, message fragmentation, and enhanced security associated with key management. The routing of messages follows the previously described cluster-tree methodology where routes to all points are maintained at each cluster. This allows a very short routing time, but requires lots of routes. Discovery of routes uses the AODV algorithm where paths are explored between clusters.
Network Architecture. The network (Figure 5) consists of three specific types of points. A ZigBee coordinator (ZC) is required for each network and initiates network formation; the coordinator may act as a router once the network is formed. The ZigBee router (ZR) is actually an optional network component, although a network without routers becomes a point-to-multipoint network; the router participates in multihop routing of messages. Finally, the ZigBee end device (ZED) does not allow association and does not participate in routing. As such it is often referred to as a child because it doesn't really have any responsibilities.
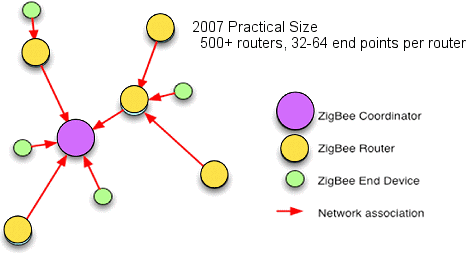 Figure 5. ZigBee network architecture |
Strengths. End devices are very low power because they are subservient to parental routers. Cluster-tree routing provides quick knowledge of routes and thereby efficient routing.
With ZigBee PRO, frequency agility switches away from problem channels automatically in a sort of on-demand frequency hopping. Message fragmentation support allows for long messages and security is flexible with support for separated keys. Finally, the network can scale to be very large.
Limitations. The biggest limitation tends to be in terms of power in the routers. Routers must be powered; they can never go to sleep. In addition, cluster-tree routing means that network changes require a lot of route discovery traffic and heavy traffic volume means lots of collisions and potential message loss. Finally, a coordinator is needed to start and manage the network, so if the coordinator goes down, no one can join and the network can't start.
Wireless HART
Key Characteristics. Gaining in popularity, Wireless HART uses the time synchronized mesh protocol (TSMP) created by Dust Networks. Unlike other networks, the time-based system uses TDMA (time slots) for an access method. The network is optimized for low power, all nodes can be sleeping routers, and every node is a router. A gateway is required to keep the network synchronized due to the critical time synchronization of sleeping and waking functions. Like ZigBee, Wireless HART is built on top of 802.15.4 DSSS, but it adds a more deliberate frequency-hopping algorithm. Security includes encryption and authentication.
Network Architecture. Figure 6 illustrates a typical network topology. Note that all the nodes are routers. The illustrated routes change dynamically based on visibility within specific time slots as the message hops through the different DSSS channels. The relationship between any two nodes is negotiated to be in a specific time slot, thereby minimizing the probability of any collisions. When sleeping, nodes awaken during their time slot and listen to see if there is any traffic. Clocks are kept synchronized by the gateway.
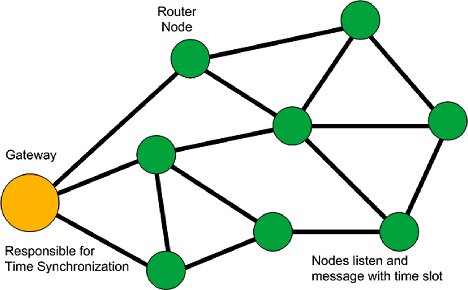 Figure 6. WirelessHART network architecture |
Strengths. Every node is a router at very low power consumption and most of its time is spent listening. Since transmissions occur only within the allocated time slot, retransmissions are minimized. Communications are very reliable, with every message acknowledged. Networks are able to scale to a moderate level or around 1000 nodes. Frequency hopping minimizes the probability of interference and security includes encryption and appropriate authentication.
Limitations. Because of the time slot approach, latency is long and nondeterministic. It takes a while for a network to form and for all of the nodes to negotiate their individual time slots. Because communications are slotted, the available 802.15.4 bandwidth is split up, meaning that throughput is minimized for bursty traffic. A powered gateway (coordinator) is required for the network to stay functioning, opening up a single point of failure if the gateway is unavailable for an extended period of time. Finally, the radios are very expensive compared to the other available solutions.
6LoWPAN
Key Characteristics. 6LoWPAN is a distorted acronym for IPv6 over low power wireless personal area networks. Presently it is a proposed standard based on the IETF RCF 4944 and designed to be used over 802.15.4 chips and radios. Unlike traditional IPv6, 6LoWPAN deals with packet size incompatibilities in message transport (128 bytes vs. a maximum transmission unit [MTU] of 1280 bytes in IPv6) and it is designed for a small memory footprint system. Today it is a point-to-multipoint architecture and will be augmented with a mesh routing scheme.
Network Architecture. Figure 7 illustrates a network topology example. Note that, at this time, it is only point-to-multipoint. Unlike the other networks discussed, Figure 6 shows an end-to-end IP-based link from a host computer to an end device (a meter in this example). The end device is directly addressable by the host computer on the far end of the network. The interworking function provided in the pictured box provides a transport change and re-packetization at the data-link level.
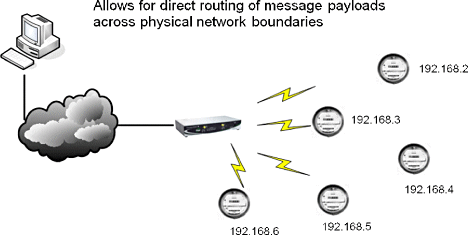 Figure 7. 6LoWPAN network architecture |
Strengths. The most powerful strength is that 6LoWPAN can take advantage of the existing TCP/IP suite of Internet protocols, all of which are well understood due to the proliferation of the Internet. For this reason it can capitalize on existing protocols, existing quality of service requirements and functions, and security framework supported by the IETF, enabling seamless routing of message payloads.
Limitations. This system is still very new and is only a proposed standard. Because it is officially in the public review stage, it will most likely undergo a number of changes. In fact, the mesh routing working groups are still being formed, which means that wide-scale adoption is still a few years away. As such, interoperability is a nice concept that has not yet been proven. Finally, because it is still new, it has not yet been ported to a large group of chipsets.
Digi Mesh
Key Characteristics. Like its sibling Wireless HART, Digi Mesh is designed to meet the need for very low power sensor networks where battery-powered routers are required. It is available in 2.4 GHz DSSS and 900 MHz FHSS. It does not rely on a full 802.15.4 implementation, as some of these functions are internal. For both message routing and discovery, it uses a variant of AODV, so routing tables are built only for needed destinations. Because of this it is referred to as a peer-to-peer mesh instead of a cluster-tree.
All nodes are viewed as equal participants; they are all routers and they can all sleep. Channel access is a sort of time-synchronized CSMA method, enabling bursty traffic, but offering few collisions. It has a full security suite.
Network Architecture. Figure 8 illustrates a typical ad hoc network topology. Unlike the cluster-tree method described in ZigBee, routes are determined on an as-needed basis, therefore routes that are never used never get routing table entries and routes that are used frequently are continuously updated, optimizing their efficiency.
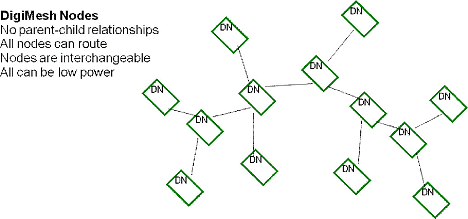 Figure 8. Digi Mesh network architecture |
One of the other important points to note is that there is no coordinator or gateway function. Time synchronization is accomplished through a nomination and election process, enabling the network to operate autonomously.
Routing Methodology. Figure 9 illustrates the process of handling routing failures. Figure 9A shows the initial network configuration where a route has been established from one point to another. Figure 9B illustrates a failure where one of the nodes has been removed for an unknown reason, removing relationships in the center of the route. Finally, Figure 9C shows how this route is reconstituted using a path that didn't previously exist. The relationships were there but they had never been used and they were newly discovered using AODV after the failure.
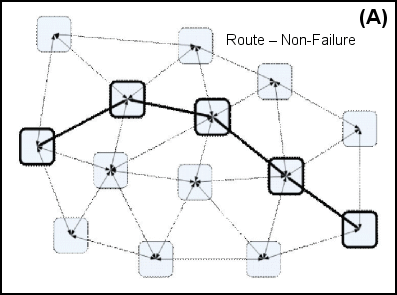 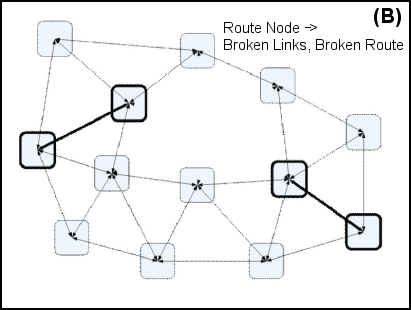 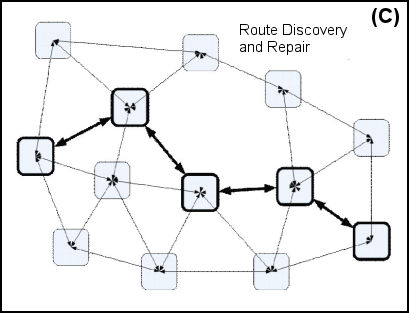 |
Strengths. Every node is a router at very low power consumption. Because every message is acknowledged and routes are determined on an as needed basis, the network is not overwhelmed with unnecessary discovery traffic, which is very important if the routers are battery-powered and sleeping. Efficient route discovery and routing means that the network learns only routes that actually get used (AODV). Frequency agility is supported and security meets the requirements of both encryption and authentication. Reliability is projected at 99.99%. Finally, the system supports larger payloads with support for message fragmentation.
Limitations. Unfortunately, efficient power management means latency is long and nondeterministic. Even though throughput is not limited by time slots, it is still limited, depending on loading and discoveries. The network can scale to a moderate size of around 500+ nodes and can be very large if traffic is light and message flow doesn't change much.
Comparison
Using the criteria defined in What a Mesh! Part 1—The Ins and Outs of Mesh Networking, Figure 10 illustrates the author's best attempt at evaluating the different network approaches. Note that they all do very well in security because they have well-defined encryption, authentication, and authorization schemes. ZigBee and 6LoWPAN get a slight nod here because their key systems should be easier to implement and a bit more flexible.
With respect to reliability, point-to-multipoint takes the biggest hit because, inherently, it has a single point of failure. Some schemes may have frequency agility options while others do not. Prior to the 2007 standard, Zigbee had a weakness in the frequency agility area; this is fixed in the 2007 standard along with adding support for message fragmentation. The others are similar: Wireless HART rates high because it is designed to never lose a message while 6LoWPAN does well on the assumption that the existing TCP/IP protocol suite has class-of-service built in. While Digi Mesh has a similar approach to Wireless HART, it is still somewhat unproven in large deployments.
Figure 10. A comparison of the five networking architectures
| Category | Point-to- Multipoint |
ZigBee | Wireless HART |
6LoWPAN | Digi Mesh |
| Security Encryption Authentication Authorization |
|
Need ZigBee PRO |
|
Use existing IP security |
|
| Reliability Freq. Agility Message Loss Adaptability |
|
Need ZigBee PRO |
|
|
|
| Power Management Sleeping Routers End Nodes Sleep Strategy |
|
Routers: 1 star End node: 4 star |
|
? Not really defined |
|
| Scalability Network Size Traffic Volume |
|
Need ZigBee PRO |
|
? Not really defined |
|
| Data Movement Data Rate Latency Range |
|
|
|
? Not really defined |
|
| Cost |
|
|
|
Assume current chipsets? |
|
Power management will no doubt be hotly debated. The nod was given to Wireless HART and Digi Mesh because they both define systems where all nodes in the network, including routers, can sleep. Even though sleeping Zigbee end devices are most efficient when it comes to power consumption, the fact that routers can't sleep caused a lower rating. Until 6LoWPAN settles on a mesh and power management strategy, the rating will remain unknown.
The scalability rating follows directly from the question of how big can the network get and still function. This is where the Zigbee PRO stack shines. The cluster-tree architecture creates a hierarchy that enables scalability. Digi Mesh and Wireless HART scale well; particularly if most communication is kept local, however, the networks tend to get very slow when they get too big. Finally, point-to-multipoint has an obvious limitation in the number of nodes that can be attached to one central point.
The best data mover is no doubt the simplest system, namely point-to-multipoint. The simple network design means that the focus can be on short, deterministic latency and high data throughput. There is a direct tradeoff here with power. Wireless HART and Digi Mesh rate lower here because they are focused on minimizing power and maximizing reliability and this naturally leads to less deterministic latency and lower throughput. I recognize of course, that as a network gets bigger, these two networks will actually do better; however, this is represented in the high scalability ratings for these networks. Zigbee fits in the middle here because the backbone of powered routers can move data very efficiently but can get stuck if too many route discoveries are needed.
Cost may end up being the most hotly debated issue. The ratings here were based primarily on the cost of available chip set solutions, assuming that the right architecture is chosen for the right job. If this is not the case then the cost ratings go out the window. For example, trying to deploy a ZigBee solution where battery-powered routers are desired means infrastructure costs will skyrocket. Given this caveat, point-to-multipoint, ZigBee, and Digi Mesh have common costs because they all use similar chipsets. The cost for 6LoWPAN is somewhat unknown, depending on resource requirements. The assumption is that chipsets similar to current chipsets can be used without substantial feature degradation. Wireless HART has a low rating predominantly because the limited number of suppliers has kept chipset prices 5 to 10 times higher than other solutions. Customers have not demanded lower costs due to nodes' primary use on expensive assets in process control environments. This will most likely change as more competitors enter the market.
Conclusion
We have traced the architectures of wireless mesh networks and the respective architectural tradeoffs. Each of the wireless mesh architectures has benefits as they optimize on different functional characteristics. There is not a one-size-fits-all approach as throughput is traded off against reliability and power consumption. Therefore, it is important to match the needs of the application to the capabilities of the network. It is also important not to settle for the wrong network because of fad or hype in the marketplace. No doubt many of the conclusions here will be hotly contested by different network architectural advocates, something that is always true where there are shades of gray in evaluating different criteria. Finally, this is a view of the state of the topic at this point in time. Had this paper been done a year ago, the results would have looked very different, as they will look different a year from now.
