
The Internet of Tiny Things
Devices such as sensors and control units in industrial environments, military applications, utility meters, and remote telemetry devices make up a large portion of the Internet of Things, sometimes referred to as the Internet of Tiny Things. The smallest of these devices are cost sensitive, frequently designed with the lowest cost CPU and the minimum amount of memory required to support their functionality, and may even be battery-powered.
Many sensors are characterized by minimal computational, memory, and storage resources. Even so, they often include TCP/IP or other communication interfaces and utilize the Internet for reporting, configuration, and control functions. As their numbers skyrocket, so has the number of cyber-attacks targeting them. Despite the growing threat from hackers, few sensor devices include robust, multi-layered security to protect against attacks. This is particularly true in the most resource constrained devices.
How Much Does It Cost?
The materials cost requirements result in devices that are resource constrained, and engineers have often forgone security capabilities in cost-sensitive designs. Many of these sensors do not support any security beyond password authentication. While password authentication is easy to implement, it does not provide an adequate defense against attacks.
Because the sensor marketplace needs a low cost, resource-friendly security to protect against Internet-based attacks, embedded firewalls provide an ideal solution. A firewall is integrated directly into the sensor's communication stack at the link layer of the supported protocol and configured with a set of rules specifying what communications are allowed or disallowed. For TCP/IP, those rules block packets by IP address, port, and protocol.
The integrated firewall provides a basic, but critical level of security by controlling what packets or messages are processed. Because each packet or message is filtered before passing from the protocol stack to the application, attacks are blocked before a connection is even established. The result is an effective layer of protection for sensor devices with minimal impact on system resources.
Next page
How A Firewall Protects Against Attacks
An integrated firewall enforces a set of rules or policies that govern who the device can talk to, what protocols and ports can be used, and who can initiate communication with the device. Embedded devices typically have very well defined communication requirements, only supporting a small number of protocols and ports.
In many cases the sensor is only communicating with a limited number of IP addresses. Some sensors need the ability to communicate with any IP address, but even then, communication is usually limited to a few protocols and ports.
Well-defined communication requirements allow the creation of restrictive firewall policies. The firewall enforces policies by filtering packets as they are received, comparing each packet to the policies, and blocking anything not matching the allowable communication policies.
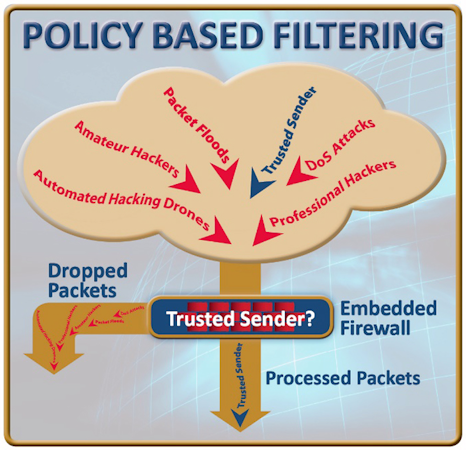
Fig.1: By enforcing firewall policies, packets from non-trusted senders are dropped, blocking cyber-attacks before a connection is established.
By only allowing packets adhering to communication policies, most cyber-attacks are blocked. A hacker attempting to log into the device is blocked because their IP address is unauthorized. Denial of Service attacks and many other cyber-attacks are blocked because they use ports or protocols rejected by the firewall, or because they originate from an IP address not allowed by the policies. When combined with password authentication, this creates an effective, resource-friendly defense against attacks.
Embedded Intrusion Detection
Sensors without a firewall or other security capabilities are an easy target for hackers. A hacker can probe these devices for weaknesses, or run dictionary attacks with no risk of detection. A brute-force dictionary attack against a sensor can be mounted for weeks, attempting thousands of login attempts and no one would ever know. An integrated firewall can report failed authentication attempts, firewall policy violations and device-specific events to a management system. That information allows detection and mitigation of attacks, providing a critical and missing line of defense for sensors.
Next page
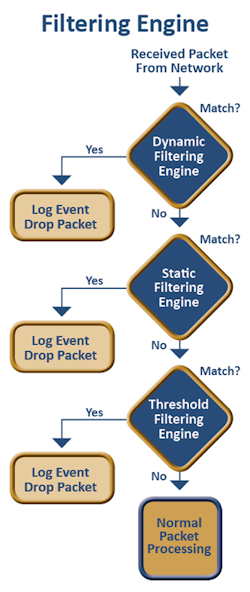 Fig. 2: Flexible and robust filtering provides sensors with a critical layer of security. |
Filtering Engine
The firewall filters packets as they are received, blocking unwanted packets, unfriendly login attempts, and DoS attacks before authentication is allowed to begin. One or more methods are implemented by the firewall to enforce firewall policies and block Internet-based attacks. Common filtering methods are:
- Static filtering: The static filtering engine compares each packet to a set of static rules determining if the packet is blocked or allowed. All decisions are made based upon the information in the packet. Rules-based filtering enforces policies by blocking unused protocols, closing unused ports, and enforcing IP address whitelists and blacklists.
- Dynamic Filtering: The dynamic filtering engine performs Stateful Packet Inspection (SPI) by maintaining information regarding the state of each connection and using that information when making filtering decisions. SPI provides protection against packets received with invalid TCP state information, a common web-based attack.
- Threshold-based filtering: The threshold filtering engine maintains statistics on received packets and monitors threshold crossings to detect packet flood DoS attacks. Threshold-based filtering is complex and may require more system processing time and memory than some systems can handle, but provides a powerful tool for detecting packet flood DoS attacks.
The firewall depends on properly defined policies allowing required communication and blocking all other communication. Defining the embedded device's communication requirements is the first step.
- With what other systems will the device communicate?
- What communication services are provided for these systems?
- Can the other devices be grouped into enclaves requiring the same services?
Once the communication requirements are specified, they are coded as a set of rules. The rules specify the IP addresses, ports, and protocols used by the device to communicate with other network nodes.
For some devices, the communication requirements are very well defined and restricted. Other devices require broader communication capabilities, resulting in broader, but not necessarily less-secure rules.
All packets received by the device are passed to the firewall for filtering and comparison to the rules. Packets not matching the rules are dropped. As a result, attempts to hack into the device are blocked before a connection is established.
Summary
For a singular example, Icon Labs provides a solution to the problems and constraints of implementing security for resource-constrained sensors. The Floodgate firewall is a lightweight, portable, product easily integrated with an embedded OS or RTOS. It is designed specifically for use on small footprint devices, even 8-bit MCUs. The firewall controls the packets the embedded system processes and blocks invalid login attempts, denial of service attacks, packet floods, port scans, and other common Internet-based threats. Floodgate also provides event reporting and intrusion detection capability, enabling detection and mitigation of threats for all even the smallest of sensors.
About the Author
David West is the Engineering Director of Icon Labs, a provider of security software for IoT and embedded devices. Icon Labs is focused on creating The Internet of Secure Things by providing security for even the smallest IoT devices. You can reach the author at [email protected].
Related Stories
2017 Security Report, Research and Roundtable
In the IoT & Beyond, Security Resides On The Dark Side, Part One
Why The IoT Is Potentially The Most Dangerous Thing In The World
In the IoT & Beyond, Security Resides On The Dark Side, Part Two
In the IoT & Beyond, Security Resides On The Dark Side, Part Three
In the IoT & Beyond, Security Resides On The Dark Side, Part Four